
[ad_1]
Many organizations have mapped out the programs and functions of their knowledge panorama. Many have documented their most important enterprise processes. Many have modeled their knowledge domains and key attributes. However solely only a few have succeeded in connecting the information of those three efforts. The rest of this viewpoint will clarify why connecting the three spheres of Information Administration – programs, fashions, and use circumstances – is so vital and the way it may be performed, by discussing the next:
- Clarification of the three spheres
- Examples of unlocked worth
- Key implementation pitfalls
- Implementation approaches
- Resolution structure parts
- Key roles throughout the three spheres
The Three Spheres of Information Administration
As talked about, only a few organizations achieve connecting the information of the three spheres of bodily programs, knowledge modeling, and enterprise processes. They fail to achieve the middle of the next determine and subsequently to unlock the potential advantages that (meta-)knowledge administration can provide.
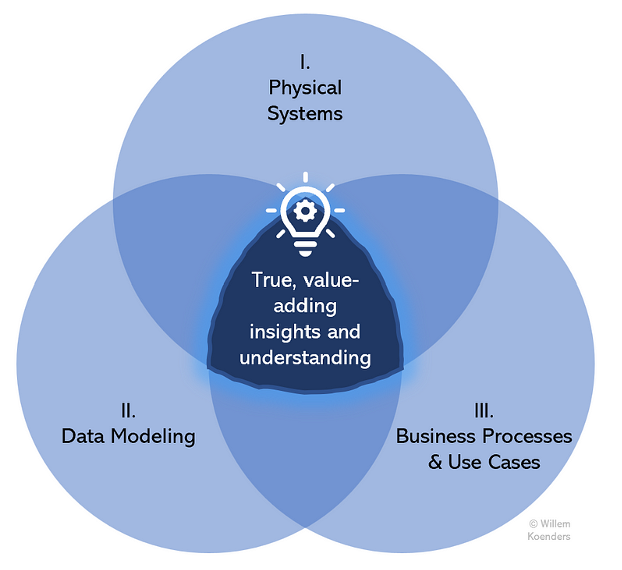
For every of the three spheres, data and metadata could be documented. They embrace the next:
I. Bodily Programs: Seize and documentation of metadata for bodily programs and functions, corresponding to desk descriptions, column names, technical metadata, knowledge lineage, knowledge flows, and entry and modifying log knowledge.
II. Information Modeling: Conceptual and logical Information Modeling, protecting and clarifying knowledge parts, knowledge domains, homeowners, and definitions. This typically consists of enterprise glossaries and knowledge dictionaries.
III. Enterprise Processes and Use Circumstances: Stock and outline of the group’s key present (and generally future) enterprise processes and associated use circumstances, typically associated to organizational divisions corresponding to buyer administration, services or products supply, advertising, finance, danger, and human sources.
Examples of Unlocked Worth
Let’s take an instance from the banking business to grasp why the three spheres mattes. I used to be just lately a part of an effort to make sure that knowledge was match for objective for a financial institution’s anti-money laundering (AML) course of. AML is a traditional instance of a enterprise course of that’s pretty far “downstream,” closely depending on knowledge from different “upstream” domains inside the financial institution. Required enter knowledge included knowledge on buyer identification, supply of funds, useful possession, and transactions. On condition that this course of is positioned downstream, the lineage was adopted again upstream, figuring out the feeding programs and knowledge producers.
Placing this all collectively, the AML course of proprietor was enabled to very clearly articulate what knowledge is required (II), for what objective (III), and thru which programs (I). This was vital to persuade regulators that the financial institution was compliant with AML rules and requirements. Moreover, the AML course of proprietor may talk clear necessities for the info by way of completeness and accuracy to the upstream knowledge and programs homeowners, securing its health for objective.
In one other instance, a chief knowledge officer within the retail sector initiated an effort to establish and activate knowledge merchandise. The primary prioritized knowledge merchandise involved advertising and customer support use circumstances that relied on numerous cuts of the shopper knowledge to allow segmentation and personalization. Contemplating these use circumstances (III), figuring out the info (II), and enabling them by one ready knowledge asset (I) is the place true worth was created because the return on advertising funding elevated and customer support was enhanced.
Pitfalls
Three eventualities exist whereby organizations have reached an space adjoining to the middle, however nonetheless outdoors it, therefore failing to unlock worth. These eventualities correspond to the three pitfalls within the under determine:
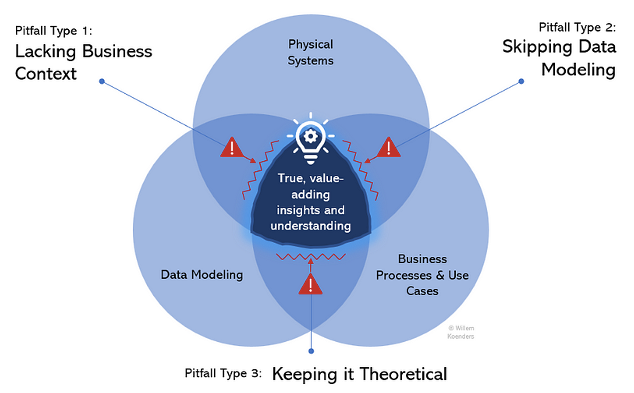
Let me describe every of those pitfall eventualities:
- Pitfall Sort 1 : Missing Enterprise Context. That is the most typical pitfall, the place bodily programs are described, and so is the info that sits inside them, however neither are matched to enterprise processes. This could occur in organizations with a Information Governance program that’s centered on creating knowledge fashions in addition to metadata associated to knowledge in bodily programs. With out express hyperlinks between knowledge parts and bodily programs on the one hand, and consuming enterprise processes on the opposite, it’s virtually unimaginable to evaluate enterprise affect, funding returns, Information High quality situation affect, and upstream knowledge adjustments.
- Pitfall Sort 2: Skipping Information Modeling. Information fashions drive understanding of information throughout programs and processes; you may take a particular logical knowledge attribute, like buyer title, and confirm in what programs it lives and what enterprise processes use it. Information fashions present clear definitions and make sure that the suitable knowledge (and solely the suitable knowledge) is utilized by the suitable consuming processes. With out Information Modeling rigor, knowledge is sure for use inconsistently, misunderstood, and improperly categorised, resulting in knowledge and system duplication, and safety, reputational, and regulatory danger. On this situation, it is likely to be recognized what programs are used for what enterprise processes, however there is no such thing as a standardized understanding of the info.
- Pitfall Sort 3: Retaining It Theoretical. On this situation, knowledge domains and fashions are outlined, and they’re additionally linked to enterprise processes or use circumstances, however the linkage to precise programs is lacking. This may be the case in organizations the place the programs panorama is especially scattered or outdated, or the place there’s a longtime, traditionally robust IT group that’s set in its methods. Failure to narrate enterprise processes and knowledge fashions to the bodily panorama will indicate that no worth could be created as a result of the true knowledge can solely be ruled in precise, bodily programs, the place it’s captured, saved, remodeled, and used. Involving IT or system homeowners early on is subsequently beneficial.
Implementation Approaches
It’s unimaginable to map all related (meta-)knowledge throughout the three spheres in a single single sweep. A number of approaches can be utilized to get to the middle of the determine for a given incremental scope, and three of them are highlighted within the under determine.
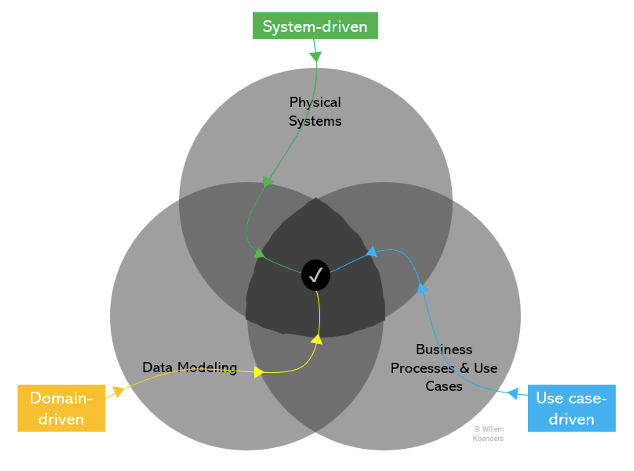
Paths to attach the three spheres and unlock true insights and worth:
- Use Case-Pushed: The AML instance I supplied earlier matches into this class. You’re taking a given current enterprise course of or use case as a place to begin, and also you establish the programs which can be presently feeding it. With programs recognized, you may establish and mannequin the info inside them. (For a new use case, you may swap the final two steps, first figuring out the required knowledge, after which drawing up the required resolution structure.)
- Area-Driven: You first prioritize and establish the info area, for instance, buyer knowledge. You then establish the enterprise processes and use circumstances, and eventually, for every of these, the programs which can be concerned. This methodology may be very a lot aligned with the recommendable greatest apply of domain-driven Information Governance, whereby knowledge is ruled primarily based on an outlined bounded context. Programs and use circumstances could change, however domains are extra steady and are usually the place knowledge possession ought to reside. Nevertheless, that is additionally the messiest strategy, as a site is a extra summary start line than a use case or system, that are extra tangible.
- Bodily programs: Begin by deciding on a system, subsequent establish the info that it holds, after which establish the enterprise processes that drive and devour from it. That is probably the most easy and best actionable strategy, as a system may be very “actual” and simple to establish. Nevertheless, there are dangers. Domains and enterprise processes are extra complete and steady – it’s simpler to compile a full record and to then prioritize them. With programs, deciding on one system over one other, within the absence of realizing what knowledge they maintain and what enterprise processes use them (as a result of keep in mind, that’s the train right here!), is a roughly random motion. In some restricted eventualities this may nonetheless be a helpful strategy, when it’s recognized a priori {that a} system is especially vital for the group; for instance, when contemplating an MDM hub or product grasp system.
In apply, organizations virtually assuredly will see efforts alongside all three approaches, and that’s completely acceptable. The important thing right here is to have a sound Information Governance and metadata administration basis whereby created information could be documented and maintained for everybody to learn from it. Such a basis could have many elements, however I’d like to emphasise two main parts of a corresponding resolution structure.
Resolution Structure
First, there’s the enterprise metamodel. A metamodel is a knowledge mannequin for metadata, which describes the core metadata objects, together with their relationships and related enterprise guidelines. In our dialogue right here, it will define how programs, knowledge, and enterprise processes are linked collectively. In a means, it offers the principles that dictate how a language could be spoken, earlier than we begin talking it. With a metamodel in place, metadata can now be found and created by the use case-, domain-, and system-driven approaches.
Secondly, there’s the metadata repository. At any time when metadata is captured by any of the three approaches, it needs to be saved in a central repository. This can drive consistency and forestall duplication. For instance, say {that a} system-driven effort mapped out the metadata for a buyer grasp system. Later, a use case-driven strategy beginning with a advertising use case identifies this buyer grasp as a feeding system. As a substitute of making a brand new, duplicate entry (and re-populating all of its metadata), the prevailing buyer grasp system can simply be referenced. A metadata repository could be instantiated by a mixture of a knowledge catalog, knowledge dictionary, and enterprise glossary.
Roles
To allow efficient knowledge administration and to achieve that airplane the place the three spheres work together, it helps to grasp the folks dimension, as a result of ultimately, particularly driving adoption, it’s all about folks. The determine under presents a view of key roles and the place they usually function.
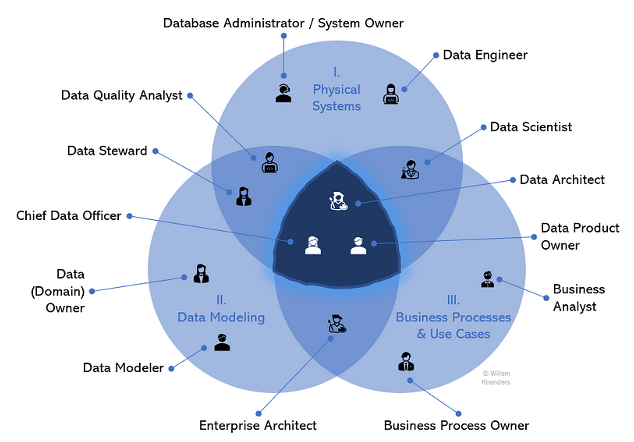
As a substitute of elaborating on every position, let me name out a number of key insights:
- Three roles, by their very definition, ought to drive the bringing collectively of the three spheres greater than any others: the chief knowledge officer, knowledge architect, and knowledge product proprietor. The CDO does this at a strategic degree — they’ve the ability to articulate why it’s vital to get to the middle of the determine, educate management, and interact executives to drive change and a data-driven mindset. The information architect can do that at a extra granular, solution-specific degree. For brand new transformations, they will make sure that for given use circumstances, the suitable knowledge is consumed from the suitable locations. As for the info product proprietor, I’ll come again to this in a bit extra element additional under.
- A number of roles are predominantly working in a single sphere. Examples are database engineers and enterprise analysts. These roles are particularly necessary to think about, as they may not naturally enterprise outdoors of their respective spheres, but they’re vital for the general framework to drive worth. Taking enterprise analysts for example, they’re vital to derive necessities for the info for respective use circumstances and to drive the final word worth creation, as their analyses needs to be carried out on the suitable knowledge from the suitable supply.
- Like several mannequin or determine, this can be a simplification of actuality. For instance, technically, any (good) Information High quality analyst wouldn’t create Information High quality guidelines with out contemplating the supposed use of the info; in spite of everything, Information High quality is the analysis of health of information for particular use circumstances. However in actuality, they’re principally working on the airplane between Information Modeling (figuring out knowledge parts and creating corresponding enterprise and Information High quality necessities) and programs (implementing for knowledge in given programs).
Connection to Information Merchandise
Greater than another knowledge idea, knowledge merchandise embody what it entails to get to the middle of the determine the place the three spheres overlap. An information product usually consists of a single system that incorporates knowledge and insights for a given knowledge area, and it features as a reusable knowledge asset that has been designed to serve particularly recognized consuming use circumstances. It’s the place programs, Information Modeling, and enterprise processes come collectively.
This is the reason the info product proprietor was positioned within the heart of the determine, and why establishing an strategy round these strategic knowledge belongings can speed up a company’s journey to unlock worth.
Conclusion
In abstract, efficient (meta-)knowledge administration requires the combination of knowledge from three spheres: bodily programs, Information Modeling, and enterprise processes and use circumstances. This unlocks the insights and worth creation that Information Administration can generate. For these organizations that haven’t sufficiently succeeded in connecting these spheres to entry their potential advantages, using a knowledge product strategy can kickstart the journey.
[ad_2]